Managed Assets ... Not Endpoints!
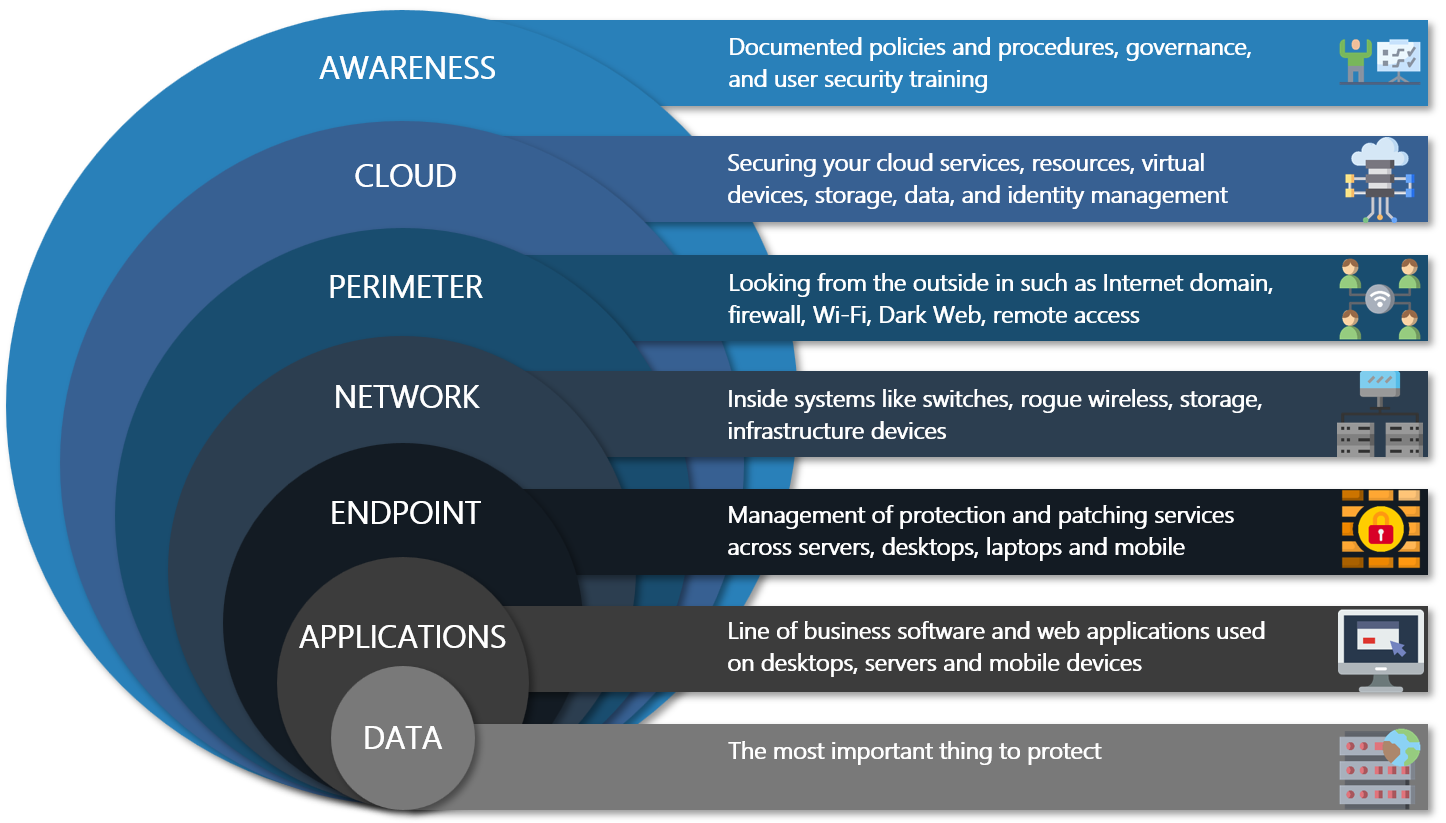
Our Proven Process
-
FIND
We identify vulnerabilities before attackers do—through deep assessments, threat detection, and continuous monitoring across your environment.
-
FIX
We quickly remediate risks with expert-driven solutions, patching gaps, hardening systems, and aligning your defenses with industry best practices.
-
FORTIFY
We strengthen your security posture long-term by implementing layered protections, automation, and awareness training—building resilience from the inside out.
Why Work With Us
-
We’re Bounty Hunters for Threats: Track and eliminate risks.
-
Built for the Real World: Tested tools, proven methods.
-
From Microsoft 365 to every device in the field, you are secured.
-
Friendly experts who care as much as you do.