Managed Assets: More Than Just Endpoints
Our comprehensive approach ensures all parts of your attack surface are continuously monitored and secured, reducing risk and strengthening your overall defense.
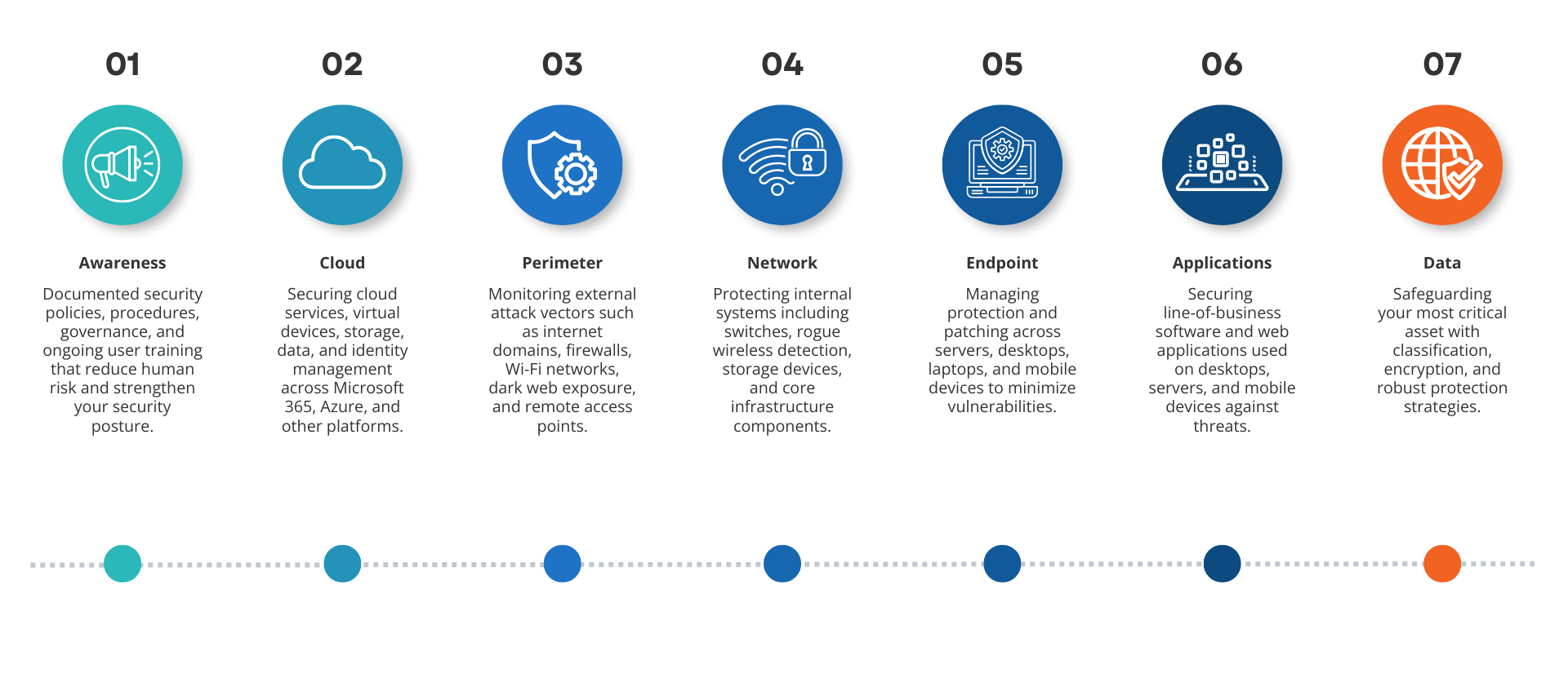
Our Proven Process
-
FIND
We identify vulnerabilities before attackers do—through deep assessments, threat detection, and continuous monitoring across your environment.
-
FIX
We quickly remediate risks with expert-driven solutions, patching gaps, hardening systems, and aligning your defenses with industry best practices.
-
FORTIFY
We strengthen your security posture long-term by implementing layered protections, automation, and awareness training—building resilience from the inside out.
Why Work With Us
-
We’re Bounty Hunters for Threats: Track and eliminate risks.
-
Built for the Real World: Tested tools, proven methods.
-
From Microsoft 365 to every device in the field, you are secured.
-
Friendly experts who care as much as you do.
Related Resources
Safeguarding Your Business: Cyber Safety Measures in the Remote Work Era
As remote work becomes the norm, cybersecurity risks are rising. We outline essential strategies to help businesses protect their data, employees, and operations in a distributed work environment.
Read More How to Build a Strong Security Culture for Leaders
In today’s threat-filled landscape, cybersecurity isn’t just an IT issue — it’s a leadership imperative. Learn how forward-thinking leaders build a culture of vigilance, transparency, and resilience to stay ahead of evolving cyber risks.
Read More Cybersecurity Challenges Resolved for Financial Institution
A leading financial institution partnered with Decision Digital to overcome rising cyber threats, compliance pressures, and internal skill gaps. Through proactive strategy, incident response planning, and managed security services, they achieved stronger protection, reduced incidents, and enhanced regulatory confidence.
Read More